![]() You don't need to be an 'investor' to invest in Singletrack: 6 days left: 95% of target - Find out more
You don't need to be an 'investor' to invest in Singletrack: 6 days left: 95% of target - Find out more
How on Earth are you meant to remember passwords these days? one I use regularly has a requirement to change every few months and have just introduced a new rule so that it automatically refuses anything similar to the old one. Of course the phrase Must have the obligatory 20 odd characters plus lower, upper, middle and symbol cases. I’m going to have to start writing them down I think.
I always have written them down.
It's got out of hand. Like all security, shortcuts get taken when it gets to much of a ballache
Get a password database then just remember that one massively important don't ever forget it or you're ****ed password.
Keychain.
There are lots of password vaults where you can save all your passwords.
It’s all MFA too nowadays. Something you know and something you have
one I use regularly has a requirement to change every few months
If you have any influence on them point them to the current guidelines on why its a bad idea.
Anyone stupid enough to ban anything similar to an old one though is living in cloud cuckoo land so a password manager would be plan b.
Store them in one of these password safe sites*
*
Which are targeted and hacked on a regular basis.
My work laptop has a password protected Excel list of all my other passwords for work. Only have to remember 9ne now. All it to auto generate random password and then just copy and paste.
My work laptop has a password protected Excel list of all my other passwords for work. Only have to remember 9ne now. All it to auto generate random password and then just copy and paste.
You can get non-cloud local-only password managers which are better suited to the job such as keepassxc ? It can also via a keyboard shortcut "auto-type" the passwords into whatever keyboard entry is in focus without any browser extension (if that kind of thing worries you). Keepassxc will can also generate passwords to specifications (length/type of character etc). Worth a look.
Get a large book.
Pick as random page, point at page randomly and select a word.
Do this three times.
Bonus ... Add page of last pic at the front or back of password.
Double Bonus ... Add a special character of your choice.
Eg.
BlueSNOWNYmountain456#
My fave book is debretts book of yachts from 1985.
If I remember correctly some US government organisation made recommendations a few years back on passwords.
21CFR11 associated rules suggested changes every 90 days. Not sure they are still the thing.
Me? I like long passwords. With random character substitutions.
Have a 'formula' that generates strong passwords but is simple to follow so that you can easily reconstruct any you forget.
Something like...
Last three letters of the website name + three words significant to you (so you remember them) with a few letters transposed to numbers. Simple to remember but generally comes up as 'strong' (Bitwarden suggests centuries to crack with a brute force effort).
Use a password manager.
Use MFA.
Read my blog posts. 😁
The company I work for now insists upon 3 words, min 8 letters long each.
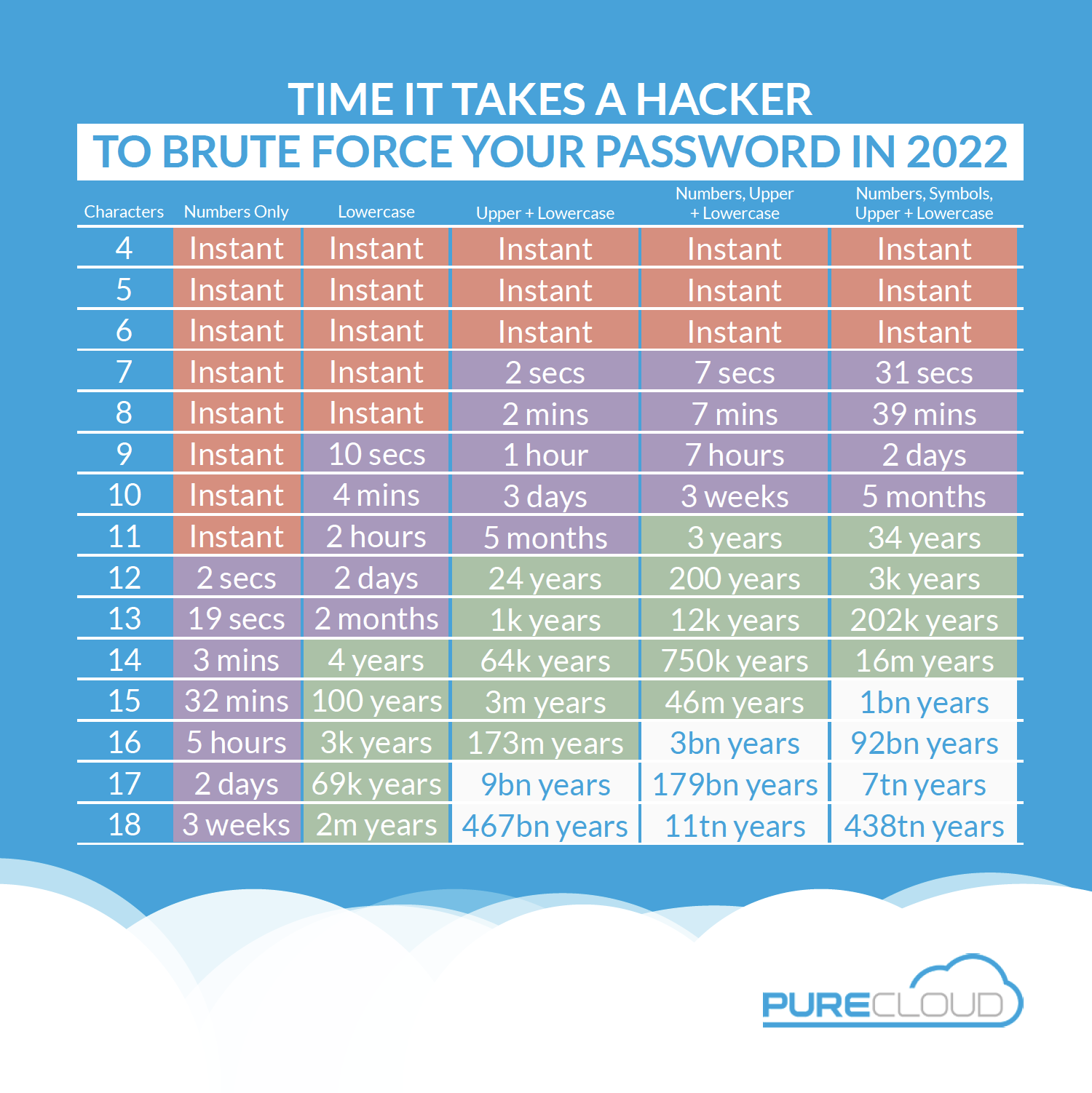
Password hacking tech is so good now that its got to be looooonnnngg.
The sums work out that a with the 60,000 words available in the english language, hacking a password of this style, at 10 attempts per second will take about 684,000 years.
Pretty secure me thinks.
Still use MFA for all my personal important stuff, bank, email etc.
I use Keychain it creates and stores them for me, I’ve absolutely no what any of my passwords are. Key chain uses upper and lower case, numbers and symbols. They’re usually around 18 characters long.
A formula or algorithm is the answer unless you want to trust a 3rd party password manager. I'll sometimes attempt to sign up to a 'new' site and it'll tell me a user is already registered with my email. Give it a couple of goes and often I'll log straight in and realise I made a purchase from them 15 years ago. You need a couple of variations for websites that want specific traits in the password, but if you go for one that is long enough and enough characters/numbers/symbols it will satisfy 90% of sites.
However, sites such as the OPs example that require regular, non similar changes you might need to do something such as break that algorithm password into three sections and insert longhand month and year or sequential trends such as colours of the rainbow so that when you change it, you can try the latest options in that list that you can easily recite. Generally these sort of sites would require you to log in frequently to avoid your account being deleted/suspended anyway
I spent yesterday going thru my Aunt's passwords as she was hacked recently.
Combination of memorable (but random) words, memorable date, symbol and Caps, plus info from the website means it's easy to remember, but different for every site.
Mine is a much longer version based on a similar formula, or apple's suggested password.
It's all a nightmare as the hackers always seem 1 step ahead....she's had a card that she hasn't used since December cloned recently. The bank can't work out how they managed it, which is scary.
Drives me mad this. It’s like an arms race to be annoying. Even when technology evolves to provide a solution (keychain), websites will evolve to undermine that convenient and perfectly secure solution. - Please enter your PIN. No memorable or consecutive numbers obvs 🙄 - Please enter the third, seventh, second above ninth characters from the grid reference of the location of where you bought your first car…
And of course, the website won’t be anything remotely important.
So you end up emailing yourself sensitive information all the time or having loads of little text files all over the place.
And don’t start me on “you have not entered a correct postcode” you then have to work on every possible permutation of spacing.
If that message pops up ,give me an example of the ****ing spacing you want.
Unless I am missing something:
similar to an old one
means they are storing the password itself not a hash of the password which is incredibly bad security practice. I’ve never heard of anyone doing this - is it actually not on any of the previous x passwords? To stop you just swapping between Password1 and Password2 every time?
NIST guidance has, I think changed recently to recommend longer, more complex passwords, but only changed is necessary. So you can do the "three words slammed together with caps and numbers and specials" to get an 18+ character password/phrase and just use that until there is a reason to change it.
Obviously you want to make that unique to each site, but having a minimum distinction between work and personal is a good thing too. MFA all the things. Good MFA too, not this cheap knock-off stuff you get on Sunday markets. Spend the extra and buy the Waitrose Premium stuff.
Chuck in a few darkweb-level unfathomable capchas for good measure. Then when you type in your passcode wrong, because you’re having to guess, a klaxon sounds and shuts everything down. YOU HAVE INCORRECTLY ENTERED YOUR PASSCODE. CALL 0900 874 6385 BETWEEN THE HOURS OF 10AM AND 2PM TUESDAY TO WEDNESDAY QUOTING YOUR PASSCODE. YOUR SECURITY IS PARAMOUNT HERE AT ABDULS TANDOORI
Ahh the good old days where my password for everything was ‘pizza’. Then it had to be ‘Pizza’ then ‘Pizza1’ then ’Pizza1! then ‘Pizza1!1980’ then… oh FORGET IT!
If that message pops up ,give me an example of the **** spacing you want.
See also, "your password does not meet the complexity requirements." Tell me what they are, I'll meet them!
FWIW, I disagree with the use of the lists that stop you using a password that has been in a breach and have told both MS and SpecOps Software that. People should use a good, strong, long passphrase, but should not be penalised if the same password has been used in a breach by another user with a different username. Besides, if they are using a decent passphrase, it should not really impact them, so it's just a means of catching the results of people being lazy.
And then MFA should give you the extra help.
NIST guidance has, I think changed recently to recommend longer, more complex passwords, but only changed is necessary.
This has been the policy at my workplace for a while. They gave up on forced password changes because there were too many instances of people sticking the latest iteration on a post-it note on their monitor.
I do like password managers, but I was stumped the other day when Plus-Net asked for two specific characters from my password during a phone conversation. In the end I had to go look it up and ring back whilst sat in front of my laptop.
FWIW, I disagree with the use of the lists that stop you using a password that has been in a breach and have told both MS and SpecOps Software that.
On what basis? The reason that's done is those passwords are included in dictionary attacks so it no longer matters what entropy they have, they'll be cracked instantly.
My work got rid of the policy to change password every month a few years ago, I used to have to update about 6 passwords every month but now it's all single sign on so I just have to remember one.
Ironically I still have to occasionally log in to an external website (a large bank) who make me change my password every month. I have to write this down as I'll never remember otherwise.
Recently got locked out of my chromebook as I'd forgotten my password, none of the ones on my phone seemed to work, despite being for the same account.
So I started the "forgot password" routine. Eventually I get to reset the password, then it asks me to enter my OLD password otherwise it'll wipe all locally saved data from my chromebook, (files, photos, apps etc) but I'd still be able to access my account.
If I could remember it, I wouldn't have clicked "Forgot password".
So I lost everything that wasn't saved to the memory card storage.
W*nkers
Absolutely no reason to faff with this when services like 1Password exist.
If you use a password manager, consider having a character that is common to each password but which is not stored within the password manager.
E.g.
Stored: A%£*Ed88gjah
Actual: AZ%£*Ed88gjah
Little bit of inconvenience but if the password is stored "correctly", then the two hashes are completely different.
Anybody else started using Passkeys now that Google has started rolling them out?
mac only, but the passwords themselves are stored in an encrypted file which i've put on icloud, so its stays synced across all my devices, and any new ones magically have it too.
On what basis? The reason that’s done is those passwords are included in dictionary attacks so it no longer matters what entropy they have, they’ll be cracked instantly.
Security vs usability.
If you had a deny list of every password that had ever been leaked in previous breaches, no-one would ever be able to create a new password without some form of password manager (which of course in many cases is no bad thing, but not always possible).
, then it asks me to enter my OLD password
Get that all the time with my elderly parents. Whether I can remember the old password when going through gmail a/c recovery hinges on who last reset it for them. Then 2/m fa really can make things overly complicated for them.
I used to work in the defence sector where we’re were dealing with classified documents. The MoD security bods insisted that we change passwords every 90 days and these would be some random, automatically-generated 20 character string too long and complex to remember. Most people had it written down on a Post-It stuck in the back of their notebook, or quite commonly, stuck on the their laptop.
I used iCloud Keychain at home across all our Apple devices. The only issue I’ve ever encountered was when my original 2012 MacBook died and there was lots of music on there we’d downloaded, but for some reason not synced to iTunes. I removed the old SSD and plugged it into a caddy to find that it required the original iTunes password from 11 years ago - fortunately I still had the old, pre-Keychain notebook where we used to write them down 🤓
Security vs usability.
If you had a deny list of every password that had ever been leaked in previous breaches, no-one would ever be able to create a new password
I disagree - it's highly unlikely a user would choose a decent passphrase (whether 3 completely random words or even with some link to themselves) with character replacements etc. that are in a cracked password file. For sure if the user is trying Pa55w0rd1! or something then it's likely to be in the cracked file but then that's a poor password that they shouldn't be using anyway so preventing them being able to is a good thing.
I do agree more helpful prompting of password requirements (or even specifically stating the password in a known bad one) in some systems would be good though.
MFA utilising simpler passwords that don't expire is the best way to go but not everywhere has the option to use MFA (including many highly classified government systems which really have no excuse but they also generally self-accredit so seem to pick and choose what best practice applies to them...)
The company I work for now insists upon 3 words, min 8 letters long each.
Password hacking tech is so good now that its got to be looooonnnngg.
The sums work out that a with the 60,000 words available in the english language, hacking a password of this style, at 10 attempts per second will take about 684,000 years.
It's a false sense of security though:
a) The actual number of words you use regularly is more like 1000*.
b) Phishing is far more likely
I'm surprised more businesses don't require hardware keys, or at least your ID badge to log in (which would also solve the problem of people leaving their PC unlocked when making tea).
*the actual number for a native speaker is apparently upto 15,000. But 1000 is apparently all you need to actually appear fluent in a language.
I disagree – it’s highly unlikely a user would choose a decent passphrase (whether 3 completely random words or even with some link to themselves) with character replacements etc. that are in a cracked password file.
I would genuinely love to test that theory.
For sure if the user is trying Pa55w0rd1! or something then it’s likely to be in the cracked file but then that’s a poor password that they shouldn’t be using anyway so preventing them being able to is a good thing.
But it meets complexity requirements!