![]() You don't need to be an 'investor' to invest in Singletrack: 6 days left: 95% of target - Find out more
You don't need to be an 'investor' to invest in Singletrack: 6 days left: 95% of target - Find out more
[b]Meet “badBIOS,” the mysterious Mac and PC malware that jumps airgaps | Ars Technica[/b]
http://arstechnica.com/security/2013/10/meet-badbios-the-mysterious-mac-and-pc-malware-that-jumps-airgaps/
Wow, that's insane.
shit the bed, incredibly clever stuff but a nightmare for IT folks.
We are doomed ... 🙄
Some clever stuff, for sure.
I'm calling bollocks on the evidence as stated.
Ignoring the separate issue of frequency response of laptop speakers and mics. How are ultra high frequency signals going to get past the input and output filters on the class D drive amp and the mic DAC?
These signals, why no scope plots, no details of transmission speeds, encoding methods? It just sounds far too wooley at the moment to me.
If the guy is geeky enough to believe this is the transmission method, he's geeky enough to either have already done these trivial tests or knows someone who would be able to do these tests. Just seems far to lacking in detail for the claims being made.
Should I get some face masks for my computer then?
What's with all the missing words & lines of text in that article...?
I reckon it's the cleaner ****ing with them. He just reinstalls the virus in the evenings.
I read that the NSA have made aluminium foil manufacturers change the way they make the stuff so that they can still access your data and mind even with extensive foil based shielding in place.
I'm calling bollocks on the evidence as stated.
+1
I read that the NSA have made aluminium foil manufacturers change the way they make the stuff so that they can still access your data and mind even with extensive foil based shielding in place.
I buy my tin foil from Russia Today though, so it's okay.
Some of it sounds plausible to me.
Dodgy USB memory stick/drive or a dodgy copy of an operating system install disk. Then combine that with the NVRAM associated with a UEFI and you could have something that's resident no matter how often you wipe or replace the HDD/SSD. Don't know if you can even clear the NVRAM like you can the CMOS in BIOS with a reset/removing the battery.
IPv6 could then be handy to get to other machines on the same network as most OS's are now dual stack (IPv4/IPv6) and will choose a IPv6 route if available over the same route via IPv4, so if the infected machine pretended to be the local router by responding with a router advertisement it could then do a man in the middle type attack on the local machines.
Russell96, that whooshing sound you just heard was your post going right over my head! I think I sort of got the gist of what you were saying, sort of, but I could be just trying to convince myself so I don't fink I'm a fik as I akcherly is.
I'm glad there are clever bods on here who can look at an article like that, and find the plot holes, if they exist, so more gullible folk like me don't get taken in.
With tech as complicated as it is, it's impossible for laymen to know if something like this is really plausible or not. On the face of it, It certainly looks like it could be.
It's absolute bollox. If someone can show me a standard laptop being controlled via audio then I might think again but the hardware just isn't there. USB drives can be infected shocker. I'm not sure what the point of this article is.
[quote=devs ]It's absolute bollox. If someone can show me a standard laptop being controlled via audio then I might think again but the hardware just isn't there. USB drives can be infected shocker. I'm not sure what the point of this article is.
Wot my esteemed friend says.
What you've got there, boys and girls, is a Halloween ghost story.
Let's handwave the technical aspects for a minute. This has been around for three years, it's got previously unheard of infection methods, elaborate methods of propagating that defy conventional wisdom, and no-one else has come across it apart from some reasonably high-profile security expert? And no-one else has reviewed any of it?
Hogwash. If that's true I'll eat my own willy.
The last three posting were all done by me.
I had taken control of there computers and user accounts by plugging the kettle into the microwave while recording Dr Who.
Sorry if that confused anyone
Hmm - a virus that can infect Windows, OSX, Linux and BeOS, transmit itself via high frequency audio, and reappear on completely clean PCs but has only infected one company?
As cougar says, it's a Halloween story. It's so clearly a ghost story it's a bit cringe worthy.
To be fair, if a virus like that was in the wild, then it would be undetected on any computer [i]except[/i] that of someone like the guy in the article that runs a computer security firm specialising in this kind of thing.
The USB infection sounds pretty interesting, but I can't understand why it apparently took him so long to see that might be an infection vector, even if the technique used was too smart to actually be detected in any normal way.
As cougar says, it's a Halloween story. It's so clearly a ghost story it's a bit cringe worthy.
In the comments the journalist admits he is skeptical too, but flat out denies this is just a Halloween hoax.
To be fair, if a virus like that was in the wild, then it would be undetected on any computer except that of someone like the guy in the article that runs a computer security firm specialising in this kind of thing.
And what's the first thing a tech would do?
"Hey guys, look at this!"
In the comments the journalist admits he is skeptical too, but flat out denies this is just a Halloween hoax.
Must be true, then.
Must be true, then.
*wheels out the vegetarian coq au vin*
It's a Halloween AND an April fool hoax then but it's defibately not true in anyway whatsoever
Okay. Let's just say I've watched enough DefCon and BlackHat videos (and worked with enough buggy flash controllers) that I wouldn't just dismiss this with a wave of my hand.
A firmware level attack makes perfect sense if you can pull it off - because you are well below what any virus scanner can detect or do anything about, and you could infect machines regardless of OS.
samuri - Member
As cougar says, it's a Halloween story. It's so clearly a ghost story it's a bit cringe worthy.
There's the thing: it requires people like you lot, who technically speaking have a clue, to point that out for people like me, who have just enough tech knowledge for it to seem plausible.
Which is why I posted it in the first place, 'cos this place is inhabited by sceptics, and if anyone could see through it, it would be someone in the STW Massive. 😀
But you know enough about computers to know you can't infect one by playing it a tune don't you?
Edit: to graham,
It can't be that difficult. I've watched independence day.
I've just hacked my toaster by humming at it.
It now goes all the way up to 11.
But you know enough about computers to know you can't infect one by playing it a tune don't you?
I do.
I haven't read the background articles posted by the researcher, I might take a look tomorrow, but my impression from the article was that the audio-networking-thing wasn't an initial infection vector, but [i]may[/i] have been used to allow infected machines to communicate with each other when they were not networked. (Though the evidence for that in the article itself seems a bit flimsy!)
The BIOS dumps are now available for download, if you fancy risking it.
I think it's real. As [url= http://blog.erratasec.com/2013/10/badbios-features-explained.html#.UnLymShX-pg ]this[/url] guy puts it - nothing you're reading about is that hard for those that have the will.
[No I don't usually wear tinfoil, worry about HAARP or chemtrails - but I do worry about virus' trashing my PC]
A quick bit of reading suggests the BIOS/ACPI rootkit is at least possible:
And as for the sound-network thing... well.. [url= http://www.soundcardpacket.org ]maybeee[/url].. but I remain unconvinced on that one till I see some scope traces!
I wouldn't just dismiss this with a wave of my hand.
I wasn't really talking about the tech, I was talking about the techie. I know a couple of security experts, they tend to be obsessive. There's no way this has been around for three years with only one person coming across it and then not telling anyone.
The story is well written, it's outlandish without being wholly impossible. The sound communication, for instance, would seem to be technically possible (assuming the hardware can handle frequencies over, what, 20KHz?) but it would require an initial infection by other means in order to start listening in the first place, so it begs the question as to why anyone would bother other than because they could. Or there's the BIOS attack; a BIOS is pretty basic (that's what the B stands for) but there's been at least one common in-the-wild virus (CIH / Chernobyl) and there's a thing called the Persistent BIOS Infection. But IIRC most modern BIOSes and EFI require signed code, which makes that sort of shenanigans much more difficult than they used to be.
I'd be more inclined to believe it if it was a single new tech; the EFI attack for instance, or the aforementioned comms, or a BIOS attack, but all these things together? Possible perhaps, but bloody unlikely.
IMHO.
Security expert confused by cutting edge BIOS virus....LOL.
Security expert confused by USB drive propagation of virus....moar LOL!
Cutting edge stuff that..............15 years ago. Not as cutting edge as psychic computers that can communicate with each other with the power disconnected. Man that's good.
Fortunately I have encountered all of this before and the answer is to put the infected PCs into a freezer for at least 24 hours to kill off the infection. Or expose it to absolute zero for 1 second. Make sure that you put it in a waterproof back though as the condensation when you take it out could damage it. Sonic screwdrivers work also.
Cutting edge stuff that..............15 years ago.
So why are lots of other security experts intrigued by it and wanting to know more?
You realise that when you say "[i]USB drive propagation of virus[/i]" we're not talking about something obvious that a virus scanner would catch, like an autorun file. The attack he describes doesn't use files, instead it infects the microcontroller on the USB stick. I thinks that is fairly new.
Not as cutting edge as psychic computers that can communicate with each other with the power disconnected. Man that's good.
Again you realise when they say "power disconnected" they mean laptops running on batteries? Not exactly fantastical that.
Like I said skepticism is always good, particularly on the internet, but dismissing this out of hand is almost as naive. Personally I'm interested enough to see what evidence emerges from other sources with the release of the BIOS dumps.
I read that the NSA have made aluminium foil manufacturers change the way they make the stuff so that they can still access your data and mind even with extensive foil based shielding in place.
Holy tin foil Batman!
As cougar says, it's a Halloween story. It's so clearly a ghost story it's a bit cringe worthy.
* Starts working on a film script titled Breaking badBIOS *
Yep, that USB Condom is a good idea*, but only really useful for something you [i]only[/i] want to charge from USB.
*(assuming you trust the implementation, the microcontroller on it isn't writable, and/or the data lines are not physically connected at all)
I know man, but still, I got to post it without going O/T 🙂
Despite being far fetched, it's plausible.
People thought malware designed to corrupt industrial applications was a fantasty - until Stuxnet was discovered. That relied upon several Windows XP exploits (one of which was still undiscovered) to work on the target.
I should have added 3 years to suss out infection via USB FFS! but for once I was trying to be a bit diplomatic and limited it to some of it seems plausible.
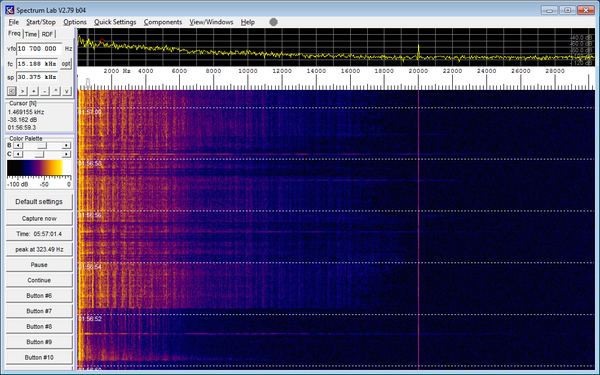
Couple of demos from the ErrataSec guy:
[b]Robert David Graham ?@ErrataRob
[/b]
Left notebook receives 20khz carrier generated by notebook on right while dubstep plays background:
[img]:large[/img]
Closer look, showing 20khz carrier visible. This is NOT #badBIOS, just a simulation showing ultrasonic coms possible
-- from Twitter: https://twitter.com/ErrataRob/status/396157617283686400
Interesting stuff!
Again, no one is arguing about the technicslities of this. Not of the technical stuff sounds particukarky difficult although the communication over audio seems pretty pointless..
That it's been going on for three years and this he's has been investigating for weeks tells you that something is amiss. hes not the only security expert out there but hes the only one who is paying this much attention.
Believe it if you want. I've got tens of thousands of devices to protect and I'll focus on the real threats.
The individual elements sound feasible to me. I say plausible.
virus checkers could be made to validate bios for this. Ultimately, it's just a new vector for a virus.
interesting read. have also watched defcon/blackhat type vids, plus watch hak5 pretty much every week, so all though far fetched, i could certainly believe parts of it.
funnily enough the Hak5 ep i was catching up on just 2 days ago was exactly this... communicating with a laptop that has no wireless or wired network connection, and no USB. one method was audio, but in audible range, and the other was via 2D barcodes and webcam.
It may have had USB, but that is definitely an attack vector too. Especially as every single machine out there independent of OS (Mac, Linux, Windows, Solaris, BSD, ... doesn't matter) has one interface that is automatically always trusted.
[url= http://blog.erratasec.com/2013/10/badbios-features-explained.html ]http://blog.erratasec.com/2013/10/badbios-features-explained.html[/url]
some more on the topic
I'm amazed that in 3 years he hasn't managed to dump the BIOS from one of his "infected" machines and just compare it with what's supposed to be in there, hence I'll keep my cynic hat on for now.
People thought malware designed to corrupt industrial applications was a fantasty - until Stuxnet was discovered.
No, they've been theorising this and in some places taking it quite seriously for years.
There are many ICS infection vectors that were around long before Stuxnet. Stuxnet used not one but three zero day vulnerabilities to propagate, that's how serious hackers with multi-million pound development budgets go about their business. They assign targets, they keep their secrets secret and they attack targets worthy of the investment they have put in.
They don't spend years developing highly advanced attack methods and then pass it over to a small time security researcher.
virus checkers could be made to validate bios for this.
Not so sure. If a virus checker has to make BIOS calls to check the contents of the BIOS then it'd be possible for the virus to hide itself like rootkits do.
I'm amazed that in 3 years he hasn't managed to dump the BIOS from one of his "infected" machines
Possibly the same kind of issue? Dumping the BIOS from software requires issuing BIOS commands which could be intercepted. You'd need to hook up some hardware that could read the BIOS flash directly.
But you're right - 3 years sounds like a suspiciously loooooong time for a security specialist to do something like that!
I think the possibility that it is infecting microcontrollers is more concerning than the BIOS stuff, as they'd be even harder to detect. Though my cynical mind wonders why microcontrollers would shipped without blowing the write fuse on the flash first? How often do they actually do field upgrades to the firmware of USB sticks for instance?
Something else that ocurs to me at this point - webcams. If you leave a room with a few machines in running this sort of exploit then singalling using using video output and webcam input is also possible - even if it's a frame or two of a QR code after 10 minutes of inactivity - hell you if you're monitoring the webcam you can look to see if anyone's in the room and not using the machine.
It's the mesh aspect of this I don't like.
As samuri says real threats are more important - we don't know what if anything this does apart from reconstruct itself; but I was talking with my "tame hacker" a few weeks ago and we were pondering what would happen if all the firewalls came down. This stuff is a step in that direction.
I'm not saying I'm going to do anything at this point, but I am, shall we say, interested in the fallout from this article.
Yo - samurai - what if he's got it on his machine by accident. You know, Hanlon's Razor?
[i]How often do they actually do field upgrades to the firmware of USB sticks for instance? [/i]
Never would be my guess. I'd be very surprised if USB stick (rather than more advanced USB devices) prom's are even programmable.
Could be wrong of course but it's simply an extension of the USB bus at the end of the day.
[i]Yo - samurai - what if he's got it on his machine by accident. You know, Hanlon's Razor?[/i]
Possible I guess. The coincidence is extreme though.
Dumping the BIOS from software requires issuing BIOS commands which could be intercepted.
BIOS code is mapped into the processor's memory space, you should be able to just dump it with a debugger. Although given the rest of what he's saying maybe this magical malware disables debuggers! But if I was looking at it seriously I'd have ripped out a supposedly infected BIOS chip by now and read it offline.
I'd be very surprised if USB stick (rather than more advanced USB devices) prom's are even programmable.
Could be wrong of course but it's simply an extension of the USB bus at the end of the day.
Yeah me too.
Funnily enough today I'm writing unit tests for a USB driver on a MSP430 microcontroller - but that's for a device that's a bit more complex than just a USB drive.
BIOS code is mapped into the processor's memory space, you should be able to just dump it with a debugger. Although given the rest of what he's saying maybe this magical malware disables debuggers!
Yeah but the action of shadowing the BIOS to main memory requires BIOS commands. Clever malware could supply a clean version or just disable ram shadowing completely since it is usually a user-accessible BIOS option.
But if I was looking at it seriously I'd have ripped out a supposedly infected BIOS chip by now and read it offline.
Yep. Seems like the obvious thing to do if you suspect this kind of thing. Which makes me skeptical, but still interested.
so in all this time he's not shared anything with anyone else on his dodgy USB stick? if this thing is so pervasive why isn't it everywhere already?
maybe it is! 😯
😉
He unplugged the mains, but did he turn off the lights and use a battery powered torch?
Prolly some covert device making the lights flicker, and the webcam is reading the the low-bit rate optical ripple.
edit: and a backdoor in the Intel/AMD chipset to keep the NSA happy
Well we all know how long loading tapes used to take... Freakin ages for a 40kb load.
I call this bollox as the high frequencies would not be picked up by a standard mobo soundcard without you hearing it. If they can get the audio frequencies near the computer I expect they can physically infect it.
[i]after buying a new computer, he noticed that it was almost immediately infected as soon as he plugged one of his USB drives into it.[/i]
Wooo-oooo! It's a ghost!
If they can get the audio frequencies near the computer I expect they can physically infect it.
You seem to be misundertanding the point there. The hypothesis is that the audio-network-thing is for [i]already infected[/i] PCs to communicate without the need for a physical network. I don't think anyone is suggesting it is a primary infection point. That seems to be the USB.
Well we all know how long loading tapes used to take... Freakin ages for a 40kb load.
Not so long ago we were all using 56k modems that used audio to transmit data. You wouldn't want to watch YouTube HD on them - but it is fast enough for small virus payloads.
> How often do they actually do field upgrades to the firmware of USB sticks for instance?Never would be my guess. I'd be very surprised if USB stick (rather than more advanced USB devices) prom's are even programmable.
Well I had a (very careful!) look at that flashboot ru site that the ErrataSec blog linked to and it does [i]look[/i] like you are able to reprogram the controller on a surprising number of flash drives.
(Though I'm not downloading [i]anything[/i] from that site to try it!)
The early mention of booting a MacBook Air from a CD-ROM got my senses a bit tingly and moved the cycnicsm to 11 on the dial.
The early mention of booting a MacBook Air from a CD-ROM got my senses a bit tingly and moved the cycnicsm to 11 on the dial.
This +1.
I'm filing it in the "plausible but bollocks" category.
The early mention of booting a MacBook Air from a CD-ROM got my senses a bit tingly and moved the cycnicsm to 11 on the dial.
http://store.apple.com/uk/product/MD564ZM/A/apple-usb-superdrive
?
[quote=Article] A computer running the Open BSD operating system also began to modify its settings and delete its data without explanation or prompting
Anyone who knows what OpenBSD is might be amused by this...
Whyso?
Anyone who knows what OpenBSD is might be amused by this...
OpenBSD is a standard unix OS, no?
So, all you need to do is start rewriting some text files.
That would be my understanding, I think I just didn't read it as humor. Sorry.
Easy as anything to test the ultrasound theory though, surely? Just need an expensive ultrasound mic connected to a scope. Or, if this isn't total bullcrap, a cheap one pried out of a laptop 🙂
Yeah the most suspicious thing about all of this is how easy it would be to prove or disprove some of these theories, especially for an infosec consultant who specialises in this kind of thing.
And yet we've seen very little in the way of actual evidence.
All very odd.
Still, didn't stop you popping up on Naked Security and putting your oar in did it? 😉
Damn straight!
I was a bit disappointed that a Sophos blog was misreporting it.
Shows they haven't really looked at it properly.
I like the approach of the chap in the original article. Just keep plugging shit in. Whatever you do, don't stop and try a methodical approach. It could be the way the journalist writes it, but it's like reading about someone who keeps getting his wedding tackle caught in a mangle and can't figure out why.
I'll just reference Wired's article on Stuxnet again. It never fails to impress me: http://www.wired.com/threatlevel/2011/07/how-digital-detectives-deciphered-stuxnet/all/